03 Dec 2025
Digital security means protecting your digital data, assets, and systems from unauthorised access, manipulation, or destruction. In today's interconnected world, where much of our personal and professional lives are conducted online, digital security has become paramount.
It isn’t just a concern for large corporations or government agencies, digital security affects individuals and groups of all sizes. Cyberattacks, data breaches, and identity theft can happen to anyone, with devastating consequences. It’s important to put measures in place to protect your local action group and stay aware of emerging threats. Protecting your privacy and security shouldn’t be left to chance.
Here we outline the common digital security risks your group might come across and steps to mitigate them. If you have questions or need help, please contact [email protected]
Secure digital communications
As a local action group you'll likely use the internet to organise, i.e run the group and your campaigns. That puts your online communications at risk of being targeted by anyone who wants to disrupt your work. They may oppose what you’re campaigning for or try and exploit you for their own gain.
Email might be a common and easy way to talk within your group. But it might not always be the safest, depending on the sensitivity of your work because it's not as secure as other communication methods. Alongside the risks of hacking and phishing, information can be forwarded, saved and printed without your control. The risks increase if you’re using a cloud-based email service, like Gmail or Yahoo Mail.
If you're concerned about your digital communication being compromised, consider using private messaging apps like WhatsApp and Signal. These can offer more security because they offer end-to-end encryption. Messages are scrambled so that only the sender and receiver can read them.
Many local action groups already use WhatsApp to plan and run their activities. If you’d prefer something more secure, Signal tends to perform better at security tests. For example, it doesn’t share your data with third parties.
Another aspect to consider is the network you're using to send communications. Your home’s wireless network will generally be safe to use. If you want to boost your security you could explore using a virtual private network (VPN). But the key thing to remember: don't share sensitive information over public or unsecured networks – they offer far less safety and protection.
Sharing information too widely
It’s important to keep control of sensitive information and not let it fall into the wrong hands. This is particularly true of personal data, such as names and contact details.
Imagine the scenario: you've collected some sign-ups on paper and need to scan and share them with another group member. You can't just attach the files to email and send it because that's not safe. You should first protect the file with a password, then send the password in a separate message, ideally not via email.
If you’re using video conferencing tools (like Zoom, Hangouts or Jitsi) you should control who has access to the invite links. This is particularly true of private meetings. Unless your event is truly open to anyone, don't share the invite link on social media or post it online. Consider using an event booking platform like Action Network or Eventbrite to help you oversee signups and send messages to them.
Don't post username and password details online at any time. It doesn't matter what account it is, doing so will compromise it.
If you’re using cloud-based tools like Google Docs be sure to check the share settings and limit access to only those people who need it. In a similar way to sharing by email, if let everyone view or edit your work, you risk losing control of it.
Compromised passwords
It might be tempting to use simple passwords or the same password for several accounts.. But it’s safer to use a unique password for each account. Make your password strong by using a combination of letters, numbers, and special characters.
Weak passwords can compromise the security of your accounts by being guessed or attacked by brute-force. If you’re struggling with password overload, consider using a reputable password manager to securely store and generate passwords. Both free and subscriptions options are available for individuals and teams. If you’re not sure where to start, try these reviews from PC Mag and TechRadar.
You can also add another level of security to your passwords by using two-factor authentication. This often involves using an app on your mobile phone to confirm who you are when logging in.
Ideally don’t share your passwords with anyone. Take extra care where this is unavoidable, such as a group email account which multiple people need access to. For example, Climate Action Newcastle use WhatsApp groups to manage shared passwords for all the group's accounts. Use one-time links like 1ty.me to share the passwords over email and change them on a regular basis, especially when people leave the group.
Don't get locked out
A common issue for local action groups is being locked out of an account. It happens when a group member stops being involved in the group but doesn't share passwords or update who has access. North Tyneside Friends of the Earth found themselves unable to get into their Facebook page and group email account. Both were linked to just one person, with the email account also tied by two factor authentication to a phone number outside of the group's control.
There are some steps Friends of the Earth can take to help you in this situation, so get in touch. But the best solution is a actually more a human than digital one:
- Only give people access to something once you're sure they'll stick around.
- Make sure at least two people have access to every account.
- Keep a secure track of who has access to what, and by which method.
Phishing and social engineering attacks
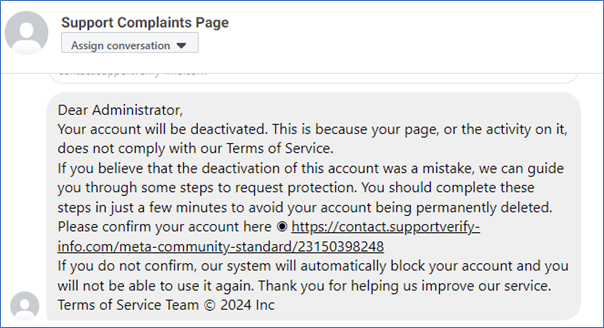
Phishing involves malicious attempts to obtain sensitive information – such as login credentials or financial details – by pretending to be a trustworthy or known source. A common tactic on social media platforms is an instant message or emails claiming that your account has been compromised or that you’ve broken guidelines. Here's a good example received by Brighton & Hove Friends of the Earth:
Social engineering tactics usually involve communications designed to make your feel a sense of urgency, fear or similar emotion. The end goal is to fool you into divulging confidential information or do something that will compromise your digital security. Because social engineering exploits human psychology, it can be challenging to identify.
Be cautious of unsolicited requests for information or assistance, particularly from unfamiliar sources or that ask for financial help. Always check that emails or messages are legitimate before taking any action , especially those requesting personal information or urging urgent action. Is the email address the message is sent from what you expect and does it match the name of the sender?
Social media platforms generally won’t ask you for your password in an email or send you a password as an attachment. If in doubt, don’t click on the link until you’ve checked where it goes. You can also detect and block phishing attempts by keeping your security software updated.
Beware of malware and viruses
Be cautious when downloading files and clicking on links from unknown sources. Be careful about opening email attachments or images. Don't trust pop-up windows that ask you to download software.
Malware (short for malicious software) is a file or code that infects a device and carries out virtually any behaviour an attacker wants. It may steal sensitive and confidential information stored on your device or install harmful software to spy on your online activities and possibly even hold your device hostage.
Use reputable antivirus software and keep it updated regularly. If you don’t know where to start, try Which? or PC Mag.
Get prepared
A good way to assess your group’s digital security is to do a risk assessment. This is best done as a group and involves answering the following questions:
- What do we need to protect?
- Who do we need to protect it from?
- How easily can they get the information, and how much do they want it?
- What happens if they get it?
- What are we willing to do to prevent them?
But mapping your answers to this chart will show you the areas where you might need to intervene and put measure in place to beef up your security. If you’d like any help with a threat modelling session like this, please get in touch with us.
One of the most common digital security risks is lack of awareness. It’s all too easy to fall for a scam or click on a malicious link only to realise too late that you’ve made a mistake. Human error and ignorance are exactly what cyber attackers are hoping for.
No system will ever be completely safe. But it’s the responsibility of everyone in your group to understand the risks. You can help achieve this through:
- Training
Make sure core members of your group know how to spot potential threats. Start by sharing this page with them and share regular updates on the latest threats out there. - Add security
Explore two-factor authentication for the group’s digital accounts that store personal information – especially email, social media and Action Network. - Communication
Ask everyone to report unexpected emails or requests for personal information that come from the group’s account. Share updates of any threats you come across.
If you find your digital security has been compromised, your first step should be minimise the impact. This could be as simple as changing a password. Or it could be more involved, such as reporting a data breach where confidential information has been exposed to a person not authorised to access it.
Keen to explore digital security further? Bueprints for change's digital security guide is a good place to start.
If you need help or have questions contact us on [email protected]